The ultimate cyber security guide: protect your data in the digital age.
1. Introduction: The Importance of Cyber Security in Today's Digital Age
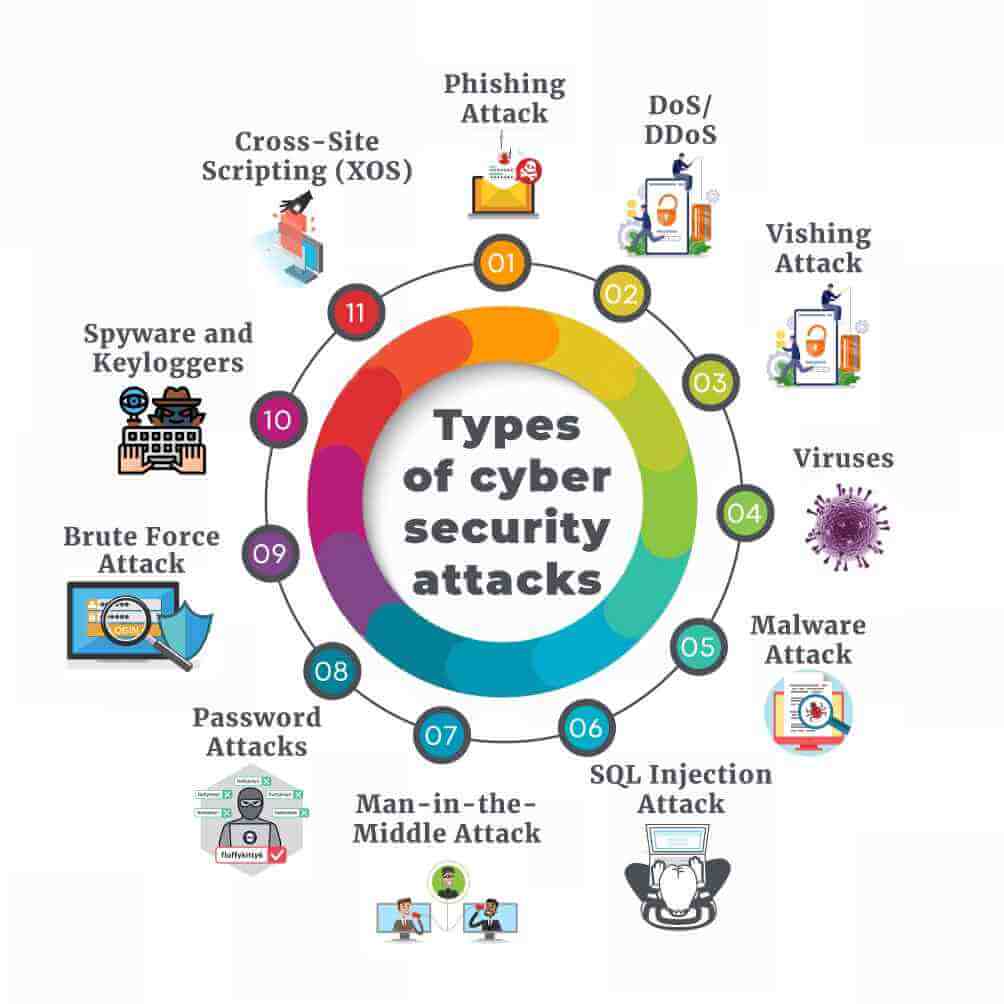
2. Understanding the Different Types of Cyber Threats
Understanding the different types of cyber threats is essential to effectively protect your data in the digital age. Cybercriminals are constantly evolving their tactics, making it crucial to stay informed and educated about the threats you may face.
One common type of cyber threat is malware, which refers to malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. This can include viruses, ransomware, spyware, and more. Phishing attacks are another prevalent threat, where cybercriminals attempt to trick individuals into revealing sensitive information through deceptive emails or websites.
Other types of cyber threats include social engineering, where attackers manipulate individuals into giving up confidential information, and DDoS attacks, which overload a network or server to disrupt its normal functioning.
By understanding these different types of threats, you can better prepare yourself and implement effective security measures to safeguard your data. In the next section, we will discuss prevention and protection measures to defend against these cyber threats. Stay tuned!
3. The Basic Principles of Cyber Security: Prevention and Protection
Now that we have explored the different types of cyber threats, it is crucial to understand the basic principles of cyber security to protect your data in the digital age. Prevention and protection measures are essential for safeguarding your sensitive information and maintaining the integrity of your digital systems.
To begin with, one fundamental principle of cyber security is to keep your software up to date. Regularly updating your operating systems, applications, and antivirus software helps to patch security vulnerabilities and protect against emerging threats.
Another key principle is to use strong, unique passwords for all your online accounts. Avoid using common or easily guessable passwords and consider using a reputable password manager to securely store and generate passwords.
Furthermore, enabling two-factor authentication adds an extra layer of security to your online accounts. This additional step, like entering a unique code or using a biometric verification method, ensures that even if your password is compromised, unauthorized access is still prevented.
Additionally, it is essential to be cautious of suspicious emails, websites, or links. Be wary of phishing attempts, and refrain from clicking on unknown sources. Always verify the authenticity of requests for personal or financial information before sharing any data.
Finally, regularly backing up your data is a crucial practice to protect against data loss. This ensures that even if your systems are compromised, you can still recover your files and minimize the impact of a cyber attack.
By following these basic principles of cyber security, you can significantly reduce the risk of falling victim to cyber threats and protect your valuable data. In the following sections, we will explore more advanced security measures and best practices for ensuring comprehensive data protection. Stay tuned for more insightful tips and strategies!
4. Implementing Strong Password Policies and Encryption Measures
In addition to keeping your software up to date and practicing caution online, implementing strong password policies and encryption measures is another crucial aspect of cyber security. Passwords serve as the first line of defence against unauthorized access to your sensitive data, so it is essential to make them as strong as possible.
When creating passwords, aim for a combination of letters, numbers, and special characters. Avoid using common phrases or easily guessable information such as birthdays or pet names. Instead, opt for a unique and complex combination that is difficult for hackers to crack.
To further strengthen your password security, consider implementing a policy that requires regular password changes. This practice ensures that even if a password is compromised, it will not remain valid for an extended period. Additionally, encourage the use of multi-factor authentication, which adds an extra layer of security by requiring an additional form of identity verification.
In addition to strong passwords, encryption is another vital measure for protecting data. Encryption scrambles data so that it is unreadable without the correct decryption key. By implementing encryption measures, you make it significantly more challenging for malicious actors to access your confidential information, even if they manage to breach your system's defences.
To ensure maximum protection, consider using encryption software or tools that are specifically designed for the purpose of securing data. These software solutions can help encrypt sensitive files and communications, making it even more challenging for hackers to intercept or decipher your information.
By implementing robust password policies and encryption measures, you add an additional layer of security to your digital systems. In the next section, we will delve into the importance of employee training and awareness in maintaining a strong cyber security posture. Stay tuned for valuable insights and strategies on educating your team to be proactive against cyber threats.
5. Educating Employees on Best Practices and Cyber Hygiene
Educating employees on best practices and cyber hygiene is an essential component of maintaining a strong cyber security posture. While having advanced security measures in place is crucial, it is equally important to ensure that employees are aware of the potential risks and how to mitigate them.
Start by providing comprehensive training programs that cover various aspects of cyber security, such as recognizing phishing emails, creating strong passwords, and identifying suspicious websites or downloads. Regularly update these programs to keep up with the evolving threat landscape.
It is also essential to establish clear policies and procedures regarding data security and privacy. Train employees on the importance of following these guidelines and regularly reinforce the message to ensure compliance.
Another effective strategy is to conduct simulated phishing attacks. These simulated attacks can help employees understand the tactics used by hackers and learn to identify and report suspicious emails or links.
Remember, cyber security is a collective effort, and an educated workforce is your best defense against cyber threats. Stay tuned for the next section, where we will explore the importance of monitoring and incident response in safeguarding your data.
and this is a full cyber security tutorial if you're interested in learning it.
6. Regularly Updating Software and Hardware for Enhanced Security
In addition to educating employees and implementing strong security measures, regularly updating software and hardware is crucial for enhanced cyber security.
Outdated software and hardware often have vulnerabilities that can be exploited by hackers. By regularly updating your systems, you ensure that these vulnerabilities are patched, reducing the risk of a successful cyber-attack.
Keep all operating systems, applications, and firmware up to date by enabling automatic updates or regularly checking for updates manually. This applies not only to computers but also to mobile devices, routers, and other internet-connected devices.
Moreover, it is essential to regularly update and maintain firewall and antivirus software. These tools act as a first line of defence against malware and unauthorized access to your system.
By prioritizing regular software and hardware updates, you strengthen your cyber security defences and protect your data from potential threats. Stay tuned for the next section, where we will discuss the importance of data backup and recovery in the event of a cyber-attack.
7. Building a Robust Network Security Infrastructure
Building a strong network security infrastructure is vital for protecting your data in the digital age. Even with the best software and hardware updates, a weak network can be a gateway for cybercriminals to gain unauthorized access to your system.
Start by implementing a robust firewall and intrusion detection system (IDS). Firewalls monitor incoming and outgoing network traffic, blocking any suspicious activity, while IDS alerts you to any potential intrusions. Together, they create a strong barrier between your internal network and the outside world.
Encryption is another crucial aspect of network security. By encrypting your data, you make it unreadable to unauthorized users even if they manage to intercept it. Utilize strong encryption protocols like Secure Sockets Layer (SSL) or Transport Layer Security (TLS) for secure communication.
Additionally, consider implementing virtual private networks (VPNs) for secure remote access to your network. VPNs create an encrypted tunnel between the user and the network, ensuring that data transmitted over public networks remains protected.
Lastly, regular security audits and penetration testing will help identify vulnerabilities in your network infrastructure. By conducting these tests, you can fix any weaknesses before cybercriminals exploit them.
In the next section, we'll delve deeper into the importance of user awareness training and establishing strong access controls to further enhance your cyber security posture.
8. Enlisting the Help of Cyber Security Professionals
While implementing strong network security measures is essential, it is also important to recognize that cyber threats are constantly evolving. Cybercriminals are always finding new ways to exploit vulnerabilities and gain unauthorized access to your data. In order to stay one step ahead, it may be necessary to enlist the help of cyber security professionals.
Cyber security professionals have the knowledge and expertise to assess your network infrastructure, identify potential weaknesses, and recommend effective security solutions. They can also provide advice and guidance on best practices for data protection, incident response, and recovery strategies.
By partnering with cyber security professionals, you gain access to a team of experts who are dedicated to protecting your organization against cyber threats. Their specialized knowledge and skills can help you detect and mitigate potential security breaches, ensuring that your data remains safe and secure.
In the next section, we will discuss the importance of creating a culture of security within your organization and the role of employee training in strengthening your cyber security defences.
9. Creating Incident Response and Disaster Recovery Plans
In today's digital age, it's no longer a matter of if, but when a cyber-attack will occur. With cyber threats constantly evolving and becoming more sophisticated, organizations need to be prepared to respond quickly and effectively in the event of a security breach. This is where incident response and disaster recovery plans come into play.
An incident response plan outlines the steps to be taken in the event of a security incident. It defines roles and responsibilities, identifies key stakeholders, and outlines the process for detecting, analysing, containing, and resolving the incident. Having a well-defined incident response plan in place can significantly minimize the impact of a cyber-attack, reduce downtime, and ensure a swift return to normal operations.
Similarly, a disaster recovery plan focuses on the recovery of critical systems and data following a catastrophic event. This plan includes backup procedures, offsite storage, and recovery strategies to ensure business continuity. By having a comprehensive disaster recovery plan, organizations can minimize data loss, mitigate financial losses, and maintain the trust of their customers.
Creating these plans requires a collaborative effort between IT and other business units within your organization. It's important to identify key stakeholders, conduct a thorough risk assessment, and establish clear communication channels. Regularly testing and updating these plans is also crucial to ensure their effectiveness.
In the next section, we will discuss the importance of employee awareness and education in preventing cyber-attacks and protecting sensitive data.
10. Constant Monitoring and Testing for Vulnerabilities
In addition to having incident response and disaster recovery plans in place, it is essential to continuously monitor and test for vulnerabilities in your organization's systems and networks. Cyber threats are constantly evolving, and new vulnerabilities are discovered on a daily basis. By regularly monitoring and testing for vulnerabilities, you can identify and address any potential weaknesses before they are exploited by cybercriminals.
There are various tools and techniques available to help you monitor and test for vulnerabilities. Vulnerability scanners can scan your systems and networks for known vulnerabilities and help you prioritize and remediate them. Penetration testing, on the other hand, involves simulating real-world cyber-attacks to assess the effectiveness of your security measures and identify any weaknesses that may have been overlooked.
It's important to note that monitoring and testing for vulnerabilities is not a one-time task. It should be an ongoing process that is integrated into your organization's overall cybersecurity strategy. Regularly reviewing and updating your security measures based on the findings from monitoring and testing will help ensure that your data and systems remain secure.
In the next section, we will discuss the importance of establishing strong access controls and user privileges to protect sensitive data.
11. Conclusion: Taking Action to Safeguard Your Data and Stay Ahead of Cyber Threats
In conclusion, safeguarding your data and staying ahead of cyber threats requires a proactive approach. By implementing incident response and disaster recovery plans, continuously monitoring and testing for vulnerabilities, and establishing strong access controls and user privileges, you can significantly reduce the risk of a data breach or cyber-attack.
Remember, cyber threats are constantly evolving, so it's important to stay informed and updated on the latest security practices and technologies. Regularly educate yourself and your employees about common cyber threats, such as phishing scams and social engineering attacks, and encourage everyone to practice safe online behaviour.
Additionally, consider investing in cyber insurance to provide financial protection in the event of a data breach or cyber-attack. It's also a good idea to conduct regular audits and assessments of your organization's cybersecurity measures to ensure they remain effective and up to date.
By taking these proactive steps and prioritizing the security of your data, you can navigate the digital age with confidence and protect your organization from potential cyber threats. Stay vigilant, stay informed, and stay secure.



Nice
ReplyDeleteThis is a very informative guide on cybersecurity! It covers a lot of important ground, from explaining different cyber threats to outlining steps to take to protect yourself. For me, the part about the importance of a national effort in cybersecurity really stuck out. Especially considering the recent rise in cyberattacks, it seems clear that Cybersecurity in the United States needs to be a major priority.
ReplyDeleteI found this information very helpful in creating my project but if this information needs to be written in a different way then a Cyber security blog can also be helpful.
ReplyDeleteThank you for this comprehensive guide on cybersecurity! It's crucial to stay vigilant in today's digital landscape. FYI Solutions offers tailored cybersecurity services, including penetration testing and phishing simulations, to help businesses protect their data and stay ahead of evolving threats. Your insights are invaluable!
ReplyDeleteHiring hackers for hire can seem like a quick fix for various tech-related problems, but it’s important to tread carefully. If you need help with cybersecurity or tech issues, always opt for ethical hackers who are licensed and operate within the law. Illegal hacking can lead to severe consequences, including legal penalties. Always verify the credentials of anyone offering these services to protect yourself and your data.
ReplyDeleteHackers for Hacker
ReplyDeleteWe are one of the best Cybersecurity consulting companies, delivering top-tier security solutions to protect businesses from cyber threats. Our expert team provides risk assessments, compliance guidance, and advanced threat mitigation strategies. With a commitment to innovation and reliability, we help organizations safeguard their digital assets and maintain a strong security posture.
Cybersecurity has become more crucial today than ever before. Having the right partners makes all the difference. At Acordis Technology & Solutions, we provide top-tier IT security services customized for your needs. Great article highlighting the importance of cybersecurity! Staying proactive is key to staying protected in this evolving threat landscape.
ReplyDeleteCyber security Miami
Great information thank you for sharing. Kloudportal = speed! Turning ideas into products 10 times faster than traditional development is a serious win for startups. Cyber security, AI and ML companies
ReplyDelete